
german version --> available OPEN SOURCE COMMONS --- GNU LINUX FREEDOM OF SOFTWARE AS AN UNIVERSAL RIGHT --- OPEN CONTENT OPEN ACCESS THE INTERNET A DECLARATION OF THE INDEPENDENCE OF CYBERSPACE --- KNOWLEDGE & COMMONS COMMUNISM & KNOWLEDGE ACCESS - Jeremy RIFKIN KNOWLEDGE VALUE CAPITAL - Andre GORZ --- SOCIETIES OF CONTROL : traditional organs with a brown history : vague legal terms - state of emergency with a brown future : new technologies – penetrate deep : biopolitical techniques – penetrate even deeper : surveillance and internet – utopia is over : closed software - closed hardware – on the short leash of corporations --- ALTERNATIVES --- BASIC TEXTS AND LINKS TO BEGIN WITH:
I would like to ask:
====
 I start from the following assumption: the earth, its treasures, its open sources and resources belong to no one, i.e., all humans -animals and plants- have the same right to use these resources. In the case of open sources, one hopes, there is enough for everyone. If not, one hopes, the resources will be distributed equally among all, i.e., there are no privileges in regard to sources. Using the example of the commons in the Middle Ages, one can imagine what belonged to the ‘open source’ at the time: ====
In the Middle Ages : community property which all community members have the right to use : paths, forests, waters, wells, and meadows were accessible to all, i.e., usage could be limited to community -or cooperative- members or be accessible to the general public. The rights of the commoners included : water rights, grazing rights, fishing rights, right to extract sand or gravel and other raw materials, right to cut peat, right to wood pasture, right to wood. PRIVATIZATION  In the 15th and 16th century, a wave of privatizing common land commenced throughout Europe. The self-sufficiency economy -subsistence economy-, particularly of small peasants -commoners-, can no longer be maintained, leading to the creation of a huge sub-proletariat that is forced to wander, to migrate to the cities, to become wage-earners or criminal.
The last commons were dissolved at the end of the 19th century, an early form of reallocating and consolidating agricultural land, the individual allotments were sold to community members. The privatization of public facilities today -railway, telecommunications- is principally no different. THE TRAGEDY OF THE COMMONS  One speaks of a Tragedy of the Commons, when one resource that was available for all becomes exhausted, because everyone will ‘naturally’ try to yield as much as possible.
is the process of commercialization or “becoming a commodity” through the privatization of resources and the capitalization of human labor -human capital-. We are today perhaps witnessing an even greater thrust of privatization than in the 15th and 16th centuries, for not only land, water and mineral resources are being privatized, but all basic resources of society that the state should actually guarantee : hospitals, education, prisons, social welfare, social security systems etc.
Less commodity-like assets are now also being commodified:
Everything turns into capital and /or a commodity, with restricted access. ====
 Open: in the early days, the 1960s and 1970s: lively and open exchange among developers and users in dealing with software. Programs, also in the form of source codes, were exchanged and adapted if necessary. That was grasped as research. Privatization: in the late 1970s and early 1980s, companies started keeping the source code of software secret and publishing it with strongly restricting licenses. ====
RICHARD STALLMAN, perhaps committed to the hippie movement and the counterculture, is the first to draw consequences from the dangers posed by privatizing the code and software: Stallman establishes GNU with the aim of developing an entirely free operating system.  At issue:
Die GNU General Public License To legally secure the idea of freedom and offer protection against privatization, Stallman drew up the GNU-GPL, a kind of copyleft principle, which obliges the users of the respective software to also pass on the freedom of the software in case of changes or when distributing it:
Starting in 1983, the GNU project was developed around the proprietary kernel of UNIX to arrive at a free, UNIX-like operating system. UNIX had the advantage that it already consisted of different, smaller programs and software components. ====
What Stallmann still required was the kernel, for it was still proprietary UNIX at the time. But then came LINUX: The original version of the source code was developed in 1991 by the Finn Linus Torvalds and published on the Internet under the free GNU General Public License -GPL- so as to motivate as many developers as possible to jointly further develop the kernel. The new thing here was foremost the joint work that then commenced and set an example for many other projects -e.g., Wikipedia-. Since that time, the LINUX kernel has been used in a number of distributions and forks. These are frequently called Linux, or more precisely, GNU/Linux system. Eric S. Raymond, a computer programmer, writer and protagonist of open source software, describes in his essay two fundamentally different types of software development:
====
is recognised by the UN as worthy of protection. It belongs to the elementary demands of civil society, with which the global digital divide is to be bridged.  One must distinguish between:
Depending on the license, free software can also be sold. However, the freedom -e.g., open source- may not be restricted when it is sold. See the various license models:  In contrast to proprietary software, when the free software is used, no money goes to foreign countries, where the offerers of proprietary software are seated. Some people see in the free software movement approaches that point to possibilities of overcoming capitalism. ====
 Free content, also called open content, does not refer to software but to texts, pictures and music, the free use and dissemination of which is allowed in regard to copyright. Either after the legal term of copyright has expired, when the originally copyrighted works count as being in the public domain. Or if the originator or the owner of the complete rights of use have placed their work under a free license. See licenses Copyleft, Creative Commons, GNU-GPL ====
 refers to the free access to scientific literature and other material on the Internet so as to use the material free of charge. In addition, there are free licenses than can enable free subsequent or further use, copying, dissemination, or also alterations to the material. Scientific publications as results of research funded by the public should in turn be made available to the public free of charge. The publication structures until now represent a privatization of knowledge financed by the general public.
The Chaos Computer Club against a state alimentation of press publishers, and also IGEL, the initiative against these ancillary copyrights. sign here: http://www.thecostofknowledge.com/ Researchers taking a stand against Elsevier
====
originated in
 Kittler : Computer software was a creation of the university, only then was it transferred to a hardware that originated in the closed circuits of military intelligence technologies.
After the ‘release’ of this hardware, the network emerges as a new space = cyberspace. A sort of black hole, an undefined ‘space’, which starts off with new, i.e., utopian possibilities but is subsequently colonized and commodified more and more. The Internet went through several development phases.
The Internet as the new and undefined land that can only be entered and altered equipped with software and hardware. The openness of this equipment is important for free view, free action, without privatistic restrictions.
The Internet became a new public space precisely at the moment when the old, bourgeois, national public was being beset, altered and fragmented by processes of globalization and privatization. structure, content, social interaction On the Internet, the developments described above converge : origin in open software, continuing participatory, collective and communicative processes to create new software and new knowledge, to create open contents, and enable free access. These collective processes generate a new wealth --> commons. This new cyber public opened up a totally new way of thinking, acting and communicating, independent of -nation--state control and hegemony, independent of territories and territorial claims to power and property, and it promises a new freedom and sovereignty, new forms of communication, existence and identity. - A utopia? ====
The Declaration of the Independence of Cyberspace was written in 1996 by John Perry Barlow, -cofounder of the Electronic Frontier Foundation, member of the band Grateful Dead - Barlow : Governments of the Industrial World, you weary giants of flesh and steel, I come from Cyberspace, the new home of Mind. On behalf of the future, I ask you of the past to leave us alone. You are not welcome among us. You have no sovereignty where we gather.
Because the Internet is still a relatively new, unregulated and open space, questions related to the -global-, -bourgeois- public are raised anew: access – access restriction, free speech – censorship, open and hidden forms of communication, copyright - copyleft, etc. Due to the infinite copyability of digital contents, questions of ownership are posed in a new way. For this reason, the way in which publics become established on the Internet, how and what they communicate, produce and exchange, is exemplary for the world outside the Internet. ====
 means that knowledge is a common good of the modern information society. As a modern commons – figuratively derived from the medieval economic form of commons – one today regards other common resources that are jointly used, including free software such as Linux or Wikipedia -collective intelligence, open content-. In this context, one also speaks of knowledge communism. ====
 The term was coined in 1942 by sociologist Robert K. Merton, and is based on the insight that research results must be published so as to check, replicate, criticize, and further develop them.
In contrast to secret research facilities of states or industries, it belongs to the essence of universities that the knowledge they generate and pass on must be able to circulate without patents and copyrights. Scientific research results thus belong to common property. Four distinctions are constitutive for the freedom of teaching and research in the sense of Humboldt: 
The crucial point of free software and open content is the detachment of the economy of ideas from the economy of goods. With its publication, knowledge becomes the common property of the community of researchers. It can be freely retraced, checked and further developed by colleagues and, in teaching, freely serve the reproduction of knowledge carriers of the next generation. Through these productive conditions in the “special milieu” of the sciences, parallel, collective efforts can lead to results that no individual or single team could produce. --> Bohemia, sub-publics- Instead of a monopolized exploitation right, as it is granted by the patent system for inventions of industrial value, the right of being mentioned by name is at the fore – a symbolic remuneration in the form of gaining a reputation as an expert. The knowledge milieus -free scientific research, teaching, publications of the researching Bohemia- radiate beyond their own fields and affect the modern, democratic society with which they emerged: Hence, the range is covered from knowledge communism of the community of researchers to basic informational services in the information society, “freedom of opinion” and related civic knowledge-related liberties and the demanded, worldwide, free flow of information. Meaning that the way in which knowledge is produced and disseminated is / was constitutive for our democratic societies. The view of the 1950s should now be assessed taking into account the Internet, free software, open access, and open content: Do these changes have an impact on our societies? Are they shaped accordingly? ====
 1. - New capitalism : right of use instead of ownership In his book “The Age of Access”, Rifkin condenses this change from the industrial age to the information age to one formula: access. Quick access to ideas, goods and services already counts more today than permanent and cumbersome ownership. Everyday life, work, leisure time, and consumer behavior are radically changing, because everything we need lies behind access barriers and is only available via paid services. This means that one no longer ‘owns’ music but pays for listening to it --> DRM-, for participating in social networks, for leisure-time offers etc. 2. - New capitalism : expropriation of the social and political The individuals’ private sphere is therefore being colonized and privatized as is the case with public space. The marketing departments utilize diverse “relationship technologies” so as to determine and control the consumption and lifestyle of the networked user. And the more private emotions and needs to socialize are marketed in the fields of image, entertainment, game and event culture, the more destructive this expropriation becomes. ====
1. - knowledge = common good = no commodity character Andre Gorz writes that knowledge is a very special resource:
This means that, as opposed to other resources that decrease when they are used, knowledge increases when it is used. The more one uses knowledge, the more one produces. So it contradicts the qualities of knowledge in two ways, when it is linked to a monetary value.
Nevertheless, in the capitalist logic, every effort is currently being made to deplete knowledge and implement access restrictions, and to subject these restrictions to a pure market and exploitation logic. To this end, knowledge is fragmented, reduced, individualized, and conveyed in a manner that limits the ability of humans to be autonomous. --> Bologna Process-  Gorz : The all but totalitarian endeavor of capital to seize hold of humans all the way to their ability to think, and the resistance that the latter offer against their own instrumentalization, mark a new and at once vague and radical form of class struggle. It evolves where knowledge is produced, shared, taught, assessed, privatized, or withheld. Where capital dominates it in that it conveys to people along with knowledge also ignorance and a sense of inadequacy: in corporations, in the educational and training system.
2. - rising unemployment = more leisure time = possible production of societal wealth -commons-
====
Knowledge is supposedly the oil of the 21st century, and we are already in the middle of distribution struggles of this highly potent resource: the commodification of universities, all kinds of patents, patents even on life, the extension of copyrights to all fields of knowledge production... All these are privatization strategies to profit from shortage. After the privatization of land and mineral resources, we are currently witnessing the probably largest expropriation process in the history of mankind. Now, the resources and services that states guaranteed for all citizens are being privatized, in particular: knowledge goods, immaterial and social goods. So that these expropriation processes can take place without hindrance, they are accompanied by all sorts of surveillance and control technologies affecting all human communication channels, our most private and our public ones, both our professional life and our leisure time: living, phoning, Internet, TV, publishing and distribution channels, and public space. (:html:)
<object style="height: 270px; width: 400px"><param name="movie" value="http://www.youtube.com/v/SGD2q2vewzQ?version=3"><param name="allowFullScreen" value="true"><param name="allowScriptAccess" value="always"><embed src="http://www.youtube.com/v/SGD2q2vewzQ?version=3" type="application/x-shockwave-flash" allowfullscreen="true" allowScriptAccess="always" width="400" height="270"></object>
(:htmlend:) TRADITIONAL ORGANS WITH A BROWN ORIGIN Founded in 1951. Even as late as in 1959, only 2 of 47 chief officers of the BKA had no Nazi past! 33 were former SS leaders. Founded in 1956 as a secret service under the direction of Major General of the Wehrmacht, Reinhard Gehlen. Renaming of his Organisation Gehlen and new identities for the former members. Former SS, SD and Gestapo officers were also employed. Investigations carried out by the Central Intelligence Agency at the beginning of the 1950s established that 13% to 28% of the staff members were former NSDAP members. A German domestic intelligence service founded in 1950. VAGUE LEGAL TERMS : STATE OF EMERGENCY WITH A BROWN FUTURE
1968 : Privacy of correspondence, posts and telecommunications, and freedom of movement may be restricted to protect the free democratic basic order. Interventions in the basic right to practice a profession are allowed.
1976: Prison sentences from one to up to ten years. The statutory offence in § 129 a stgb is controversial because no longer a criminal, but a person’s views are subject to penalty. The section is also preferably used in the frame of investigations because it encompasses a large group of persons and there are only low hurdles for an initial suspicion.
The proposal to amend the Basic Law is repeatedly made. It should be allowed to deploy armed forces domestically to be able to preventively -!- avert dangers. Plans are to deploy the armed forces to protect civilian objects, to avert immanent threats and disasters already in the preventive area, as well as to protect against threats from the air or the sea. The German Basic Law now already allows the German Federal Armed Forces to be deployed domestically in times of war to “fight against organised and militarily armed insurgents”.
Preventive custody of a person although he/she committed no crime. Although police custody must end after the end of the following day, a judge can order a prolongation of up to 14 days depending on the legal provisions of the state. In other countries, this period is extended. Critics regard preventive custody as a violation of the principles of a state under the rule of law, because it is imprisonment without having committed a crime. Talk is also of a first step from the classical state under the rule of law to a prevention state. What is also pointed out are methodical parallels to police preventive detention and protective custody that were employed against political opponents during the time of National Socialism.
Subsequent detention of criminal offenders after they have served a sentence. The purpose is to protect against further crimes. Highly controversial in regard to human rights! NEW TECHNOLOGIES PENETRATE DEEPER
A spy network -USA, UK, Canada, Australia, and New Zealand- stemming from the Cold War, with terrestrial monitoring stations and space satellites to bug satellite, microwave, and cellular radio communication. Analysis software scans the sources for relevant keywords and their combinations, as well as the thematic occurrence of the terms. Programs independently extract smallest word components from existing data sources -texts, faxes etc.- and automatically examine additional, new data sources in regard to the occurrence of the same word components in order to bring together related sources to a relevant search topic.
A method used since the 1970s for the networked search of data stocks. Certain groups of persons are filtered from public or private databases by searching for features assumed to apply to the person being searched for. The aim is to limit the group of persons to be investigated, because, as opposed to a conventional search, there is no known target subject. What is regarded as problematic in this technique is particularly the suspended presumption of innocence, for all persons to whom the features apply -e.g., shoe size, gender, nationality- are initial suspects. Only through a police check seeking to substantiate an initial suspicion is it determined whether investigations against these persons are to be sustained. The linking of data from different sources is also often deemed problematic in regard to the basic right of informational self-determination. In April 2004 it became known that after the evaluation of ca. 8.3 million datasets in Germany, preliminary proceedings were started only a single time and then abandoned again.
Bugging - 1998 acoustic surveillance of private property. Intrusion of the basic right of inviolability of the home. Critics express the fear that the amendment of the Basic Law marks the start of installing a surveillance state.
Scanning of vehicle license plates -retention- and comparison with databases through the facilities merely meant for lorry toll.
Since ca. 1980, a method to automatically identify objects and living beings. In addition to the contact-free identification and localization of objects, RFID also stands for the automatic acquisition and storage of data. Applications, for example, in passports, products in supermarkets, tickets in public transportation. Loss of informational self-determination, i.e., the individual can no longer influence which information is revealed due to ‘hidden’ senders. For this reason, the planned mass application of RFID transponders is problematic under the aspect of data protection.
With the ELENA procedure -electronic remuneration statement procedure-, starting in 2012 remuneration statements are to be made electronically with the aid of a chip card and electronic signature in Germany. But this implies : the collection of millions of employee data in a central storage, every person who participates in a strike would be recorded. The dataset includes not only, name, date of birth, insurance number, address etc., but also working hours lost, letters of caution, “inappropriate behavior”. One of the most critical points is that there is a fear of who may be allowed to access the stored data in the future. BIOPOLITICAL TECHNIQUES PENETRATE EVEN DEEPER
Machine readable with personal and biometric information.
Now also in passports -RFID-.
When entering the country and also on other occasions.
Making faces machine readable : Face recognition with CCTV to be retained. Biometric pictures also in passports.
Currently popular in England. Every citizen is to be recorded. Genetic fingerprint, DNA analysis -cigarette butts after a demonstration-.
An old trick from GDR Stasi times, again en vogue.
Devices with which the body of a person as well as objects beneath the clothes can be shown. This can visualize weapons or explosives, for example. It can be implemented using different methods.
One of a number of customer cards with personal information: discount cards, loyalty cards and member cards, bank cards, credit cards etc., mostly equipped with RFID, remote and machine readable.
Surveillance of public spaces : video surveillance, iris scan, biometrics, face recognition software and comparison, identity allocations via ‘social’ networks -f-book et al-. evaluates, among others, unemployed persons and children at dumping prices
By chronologically linking personal data from different sources, the movements -and possibly even actions- of a person can be tracked, e.g., it can be retraced when a person was at which location, what he/she purchased, and what telephone calls were made.
Astroturfing aims at giving the appearance of a civil movement or a spontaneous grass-roots movement. The impression of an independent voicing of opinions on politicians, products, services, events etc. is to be made. Like with other kinds of propaganda, the objective is to directly influence the emotions of the public. A few persons act as if they were a large number of activists, attracting attention by writing reader’s letters, emails and blog entries, disseminating crossposts or setting trackbacks. SURVEILLANCE ON THE INTERNET - UTOPIA IS OVER
ACTA is a planned plurilateral trade agreement under international law. The participating states or confederations say that, with it, they seek to enhance the fight against product piracy and copyright violations. The negotiations on the details of the agreement have been taking place since 2007 in closed sessions, so that the precise state of the negotiations is unknown. There is a fear that the international trade agreement could mark a starting point for the global implementation of Internet blocking. see also TRIPS Agreement -Agreement on Trade-Related Aspects of Intellectual Property Rights- : An international agreement in the field of immaterial property rights meant to ensure that the measures and procedures to assert the rights on intellectual property themselves do not become barriers for legal trade. Since the TRIPS Agreement took force, the WTO has been facing increasing criticism from developing countries, scientists and NGO_s. Due to the decision-making processes in the WTO, however, it is improbable that even enormous political opposition could contribute to mitigating the TRIPS Agreement.
With this act, the United States want to assert the copyright also in regard to foreign Internet sites, e.g., be means of IP blocking or DNS refusals. Opponents: Even the European Parliament stressed in a motion for a resolution at the EU-USA summit in November 2011 ‘the need to protect the integrity of the global Internet and freedom of communication by refraining from unilateral measures to revoke IP addresses or domain names’.
Access Restriction Act: with the pretext of protecting against child pornography, politicians -zensursula- are seeking to build up a censorship infrastructure to a general Censorship on the Internet.
Similar to the fixing of broadcasting times, program announcements and the indication of radio broadcasts, compulsory labeling is to be introduced for websites. The operators, like in cinemas, should offer notes and safeguards that identify age-specific accesses.
This means scanning the entire data flow all the way to the data packets to be able to filter, block or alter them in real-time. Here, DRM protected contents could be filtered, certain categories of downloads -porn or films- could be blocked, or texts in which certain keywords appear could be blocked and the content replaced -in real-time!!- by other content. For example, while calling an Internet site, the word “war” in the original source could be replaced by “armed conflict”, meaning that the copy of the original source in my browser window contains the phrase “armed conflict” instead of the word “war”.
Internet Service Providers are to be made liable for the hosted contents, meaning that they should control the contents of their clients. In addition, Internet Service Providers should be forced to give information on their users. -->connection data, data retention-
With the help of spying programs -State Trojan-, covert state interventions in other information technological systems become possible through the communication networks. The term encompasses both one-time access -online inspection- and longer online surveillance. The main critique is directed against the secrecy that contradicts the essence of investigative acts under the rule of law and various possibilities of abuse.
Spying programs smuggled into the computer by evil persons, often after visiting dubious websites or executing dubious programs of unknown origin.
The CCC found, analyzed – and hacked – the surveillance software.... more about it here: Frank Rieger : Anatomie eines digitalen Ungeziefers ... and here hier das ungeziefer Schirrmacher : Code is law-Engl-
Used for the surveillance of telecommunications. Telecommunications and Internet providers are obliged to “retain” for six months the communication data of all kinds of telecommunications: telephonic communication, connections to the Internet, email traffic, fax and SMS messages -in the case of SMS also the location-. Upon the demands of the EU Commission and the German conservative parties CDU and CSU, it should be retraceable in the future who communicated with whom in the past six months via phone, mobile phone or email, or who used the Internet. In the case of mobile phone connections and SMS, the respective location of the user should also be recorded. With the help of other data, Internet usage should also become retraceable. With the aid of data retention, the communication behavior of each subscriber can be analyzed – without access to the contents of communication. Since data is retained without an initial suspicion and the entire electronic communication behavior of the citizens can be statistically analyzed based on the data stock, this procedure is controversial in regard to constitutional law. To the extent to which communication via electronic media increases, the significance of these analyses for establishing personality and movement profiles will grow. Conclusions about the content of communication, the personal interests and the living situation of those communicating could also be drawn. Access to the data would be granted to the police, to public prosecutors and foreign states, who all hope for enhanced criminal prosecution. Brussels complains in a report that only 11 of the 27 EU countries have delivered data that suggest a surplus value of the controversial measure.
impart information of the surfing behavior of the respective user, they are extremely valuable for market researchers and cookie traders, because -especially through the combination with other data- a digital picture of the user emerges.
are malicious programs that infect the computer like trojans and can be remote controlled from outside and organized to entire networks of these malicious programs and, e.g., execute spam actions or ddos attacks.
Legal steps against alleged copyright violations on the Internet.
The demand of publishers to be able to prohibit the free use of online articles – also in excerpts. Services such as Google News that aggregate news and link them with short text excerpts to the original sources are to be prohibited or at least become subject to a charge. This would also affect blogs that cite news so as to comment on current events.
See also Heidelberger Appell of publishers and authors.
Until now, access providers have transmitted the data packets of their clients unaltered and equally, no matter where they come from or what these data packets transport. This is supposed to change. Large corporations demand that their data are given priority treatment. This would slow down the download of a film by user xyz, while downloading the same film from Amazon would be extremely accelerated. Network operators -on the Internet- see additional profits. Both the offerers -e.g., Amazon- could pay for having their contents treated as a priority and the users could purchase a subscription to quick downloads, for example. This would lead to a two-class Internet.
The FRG is the world’s THIRD-largest arms exporter. To continue war with other means, German software firms are also involved, preferably exporting surveillance software to dictatorships, e.g., German eavesdropping software for Egypt’s secret service or the funny “twitter revolution”: Siemens Nokia supplies Iran with Internet and telecommunications surveillance, a backdoor for US agencies was also installed by dropbox. As soon as M$ purchased SKYPE, Microsoft patents eavesdropping software on Skype. PRISM is a clandestine national security electronic surveillance program operated by the United States National Security Agency (NSA) since 2007 pursuant to the Foreign Intelligence Surveillance Act (FISA). NSA contractor Edward Snowden leaked that the extent of mass data collection was far greater than the public knew, and included "dangerous" and "criminal" activities in law. The documents identified several technology companies as participants in the PRISM program, including Microsoft, Yahoo!, Google, Facebook, Paltalk, You Tube?, AOL, Skype, and Apple. TEMPORA is a clandestine security electronic surveillance program operated by the British Government Communications Headquarters (GCHQ). The scope of Tempora includes recordings of telephone calls, the content of email messages, Facebook entries and the personal internet history of users. Two principal components of Tempora are called "Mastering the Internet" and "Global Telecoms Exploitation", the aim of each to collate as much online and telephone traffic as possible. The vast volume of data utilised by GCHQ in Tempora is extracted from over 200 fibre-optic cables and processed; full data is preserved for three days while metadata is kept for 30 days. The data collected by the Tempora programme is shared with the National Security Agency of the United States (NSA). STUXNET is a computer worm discovered in June 2010, it initially spreads via Microsoft Windows, and targets Siemens industrial control systems. Stuxnet is part of a U.S. and Israeli intelligence operation called "Operation Olympic Games" to attack Iran's nuclear facilities. 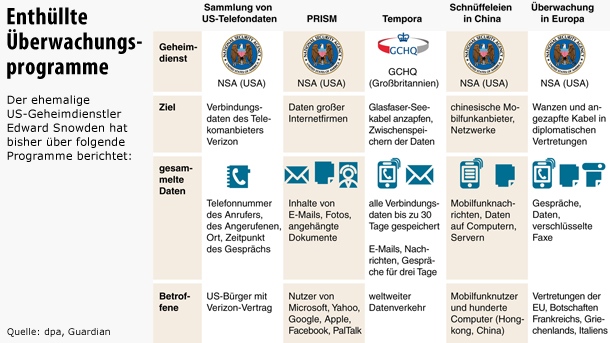 
CLOSED SOFTWARE AND HARDWARE – ON THE SHORT LEASH OF CORPORATIONS
Copy protection
is the name of methods with which the use -and distribution- of digital media are to be controlled. Particularly digital film and sound recordings, but also software, electronic documents or electronic books are subject to digital rights management.
In the opinion of the free software movement, the DRM system on principle robs people of the possibility to completely control the data and programs on their computers, thus restricting their freedom.
deletes the property of its customers: Orwell’s books “1984” and “Animal Farm” – of all books – disappeared from the memory of Kindle reading devices, although the owners had bought and paid for them. A lesson in power and rights in the age of total networking.
Trusted computing can be used to safeguard
Hardware manufacturers increasingly tend to keep their interface specifications secret to prevent competitors from imitating technological solutions. The reason for this lies in increased competitive pressure and in the fact that it is cheaper and quicker to technologically install such a protection than to reserve the intellectual property for oneself through a patent.
There is no legal definition of the concept of a software patent. Traditional patents apply to technological inventions, meaning solutions to problems the validity of which must be checked in experiments with natural forces. Software patents, on the other hand, apply to ideas, whose effectiveness can be proven solely through logical deductions. Critics such as Richard Stallman also speak of software idea patents. It must be stressed that the distinction between software concepts or ideas and software as such is an artificial one for developers, if the main emphasis is on the implementation through programming.
Microsoft’s success is predominantly based on clever market policies, it managed to sell its operating system linked to the hardware of various manufacturers. The list of infringements of the law, monopolistic anticompetitive behavior, unfair product bundling -->browser war- is so long that it can’t be dealt with any further here.
Identity concept : i-phone i-pad i-tunes i-mac. That’s I, I, I! That’s not my device, I am the device, it is a part of me and that is directly connected to APPLE. ====
Open NIC is a private network information center -in charge of assigning Internet domains-. It offers an alternative to the top-level domains administrated by ICANN -controlled by the US Department of Commerce-, it is not controlled by any national authorities and, in its own words, acts democratically. RECOMMENDATIONS darknet : serverless file sharing
anonymity and encryption
codecs:
hardware:

END It would be wrong to believe to have already won a decisive battle against political and corporate control mechanisms by using Gimp instead of Photoshop. Ideology results in structures of ownership, house, property, and money – knowledge, resources. Software and hardware condition the user, his/her thinking and actions and the resulting social changes, in everyday life and in the tides of the times. By dealing with open source, I view the world differently. I see the lines of tradition going back to the century-long battles for self-determination, to ideas of classical anarchism and communism, to life reform and Bohemia, to grass-roots and council democratic principles of organization, to collective modes of production, and common economies. With open source, one participates in a research process, a broader thought and production process, one discovers new liberties and a new wealth that has been created by a movement one can partake in – producing and exchanging... For there is no alternative : the future is self-organized! ====
---
---
---
--- compiled by s dillemuth 2011
|